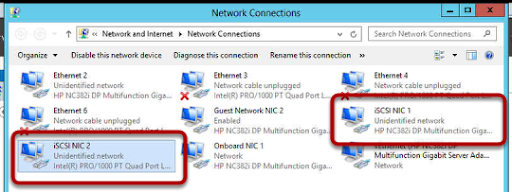
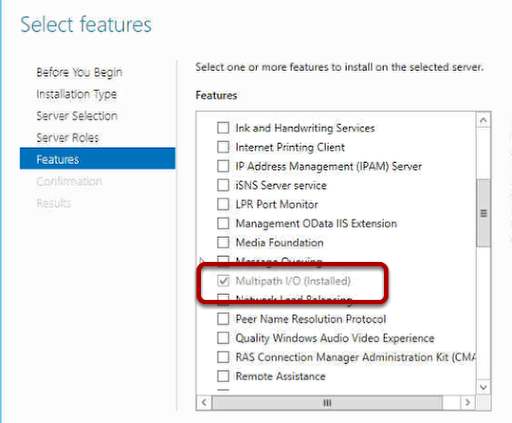
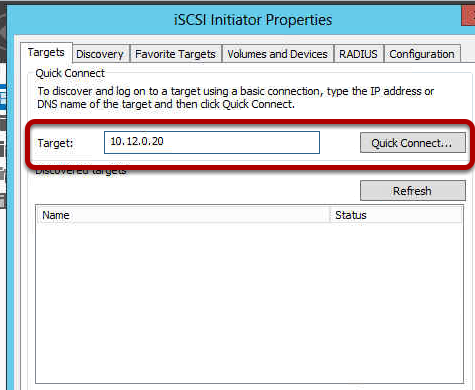
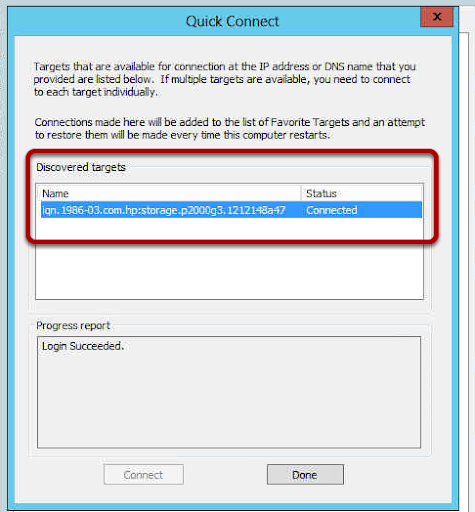
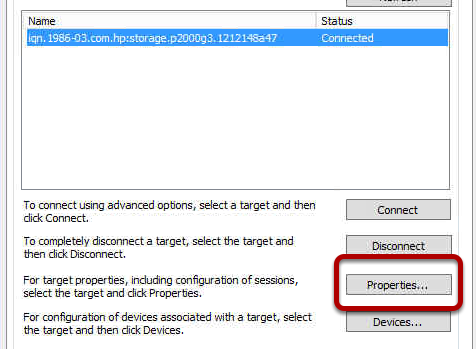
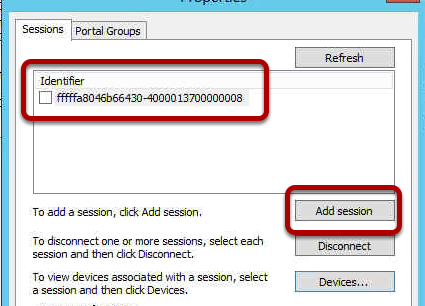
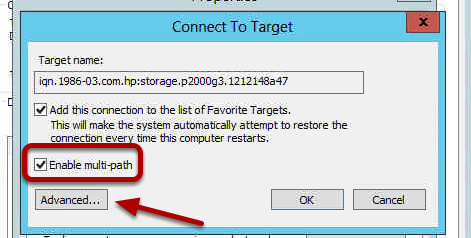
You may find when you try to activate your Windows 2012 Server that activation fails and then when you try to change your product key you cannot see how to do this. Well it turns our Microsoft have removed this by default, you cannot change your product key until you activate, you cannot activate until you change your product key. Catch 22. So what do you do?
Windows Activation
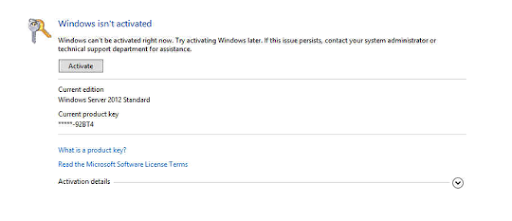
Go to the Action Center and then choose Windows Activation and you will be shown the screen above, that Windows is not activated. So we will try to activate.
Activation

Activation is attempted online.
Activation Failure
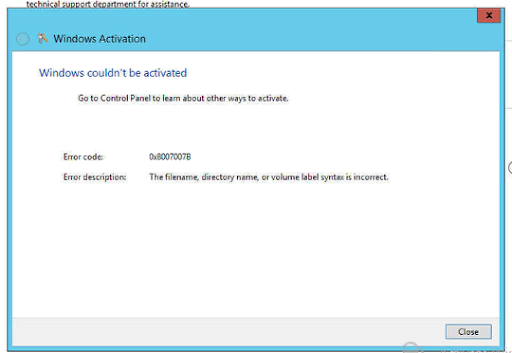
Well Windows Activation fails which is a bit disappointing, but thats OK as I didn't enter my key when I installed so I will just enter that now. Ah there does not seem to be a way to do this like there was in Windows 2008 R2. So what do I do?
The Answer
The answer is found here in this rather nice KB from Microsoft http://support.microsoft.com/kb/2750773?wa=wsignin1.0
Charm Bar
So now you need to get the Charm Bar out, this is done with Windows Key and C. Then choose the Search option.
Search
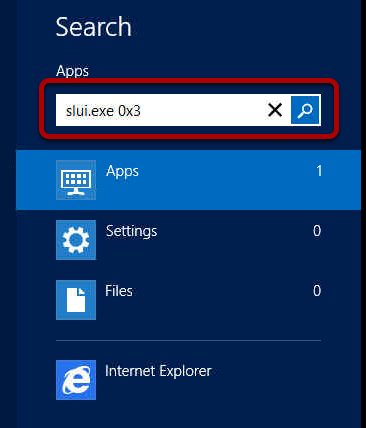
We need to search for the actual Windows Activation executable, this is called slui.exe 0x3 Don't forget the 0x3 on the end of this.
Change Product Key Time
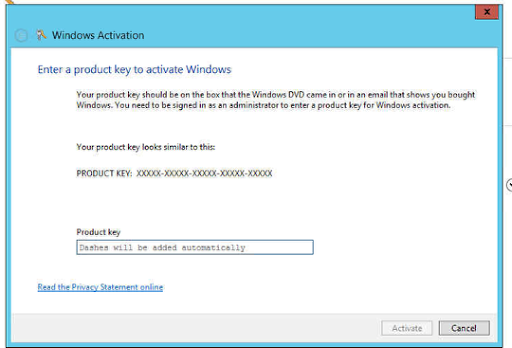
Now we can see the familiar change product key window and we can enter our correct product key.
Add Product Key
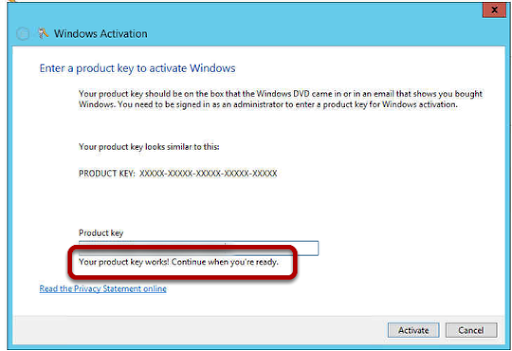
Enter your product key and it will be verifed as correct for you.
Activate
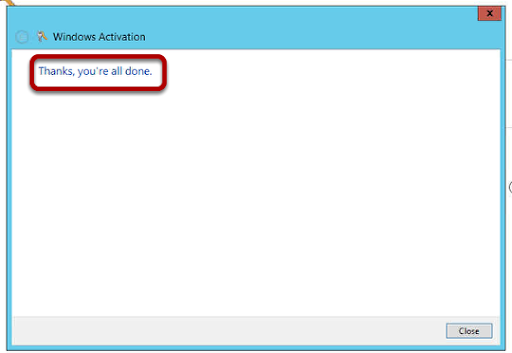
You can now perform the activation and get this cheery greeting from Redmond.